Our Proven Process Gets You Results
Our stress-free 5-step process enhances your IT so that you can log more hours where it matters most: making the world a better place.

Our Process Focuses on Prevention, Strategy and Ongoing Optimization
1. Identify
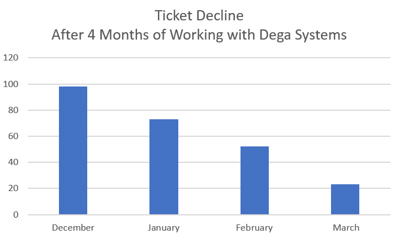
Our process begins with finding and measuring what’s creating the most IT stress and “noise” – like tech issues that need to be managed more efficiently. As you can see in the bar graph below, the organization featured was able to dramatically reduce the amount of help desk tickets after only three months of working with us (this timeline varies).
Our goal here is to help you understand that you can and should expect more from your IT systems and processes. We call this part of the process, “redefining the good.” We help you achieve this by putting in place benchmark metrics so you can measure and hold your IT accountable. This also gives you the added benefit of gaining insight into the causes of your IT “noise” and thus, the ability to resolve them.
2. Assess
What’s working for you? What’s not? Why?
This is where we start to survey and gather data on your hardware, software, and systems to better understand what’s working and what’s not.
In order to quickly get to the heart of these questions, we rely on the following assessment tools:
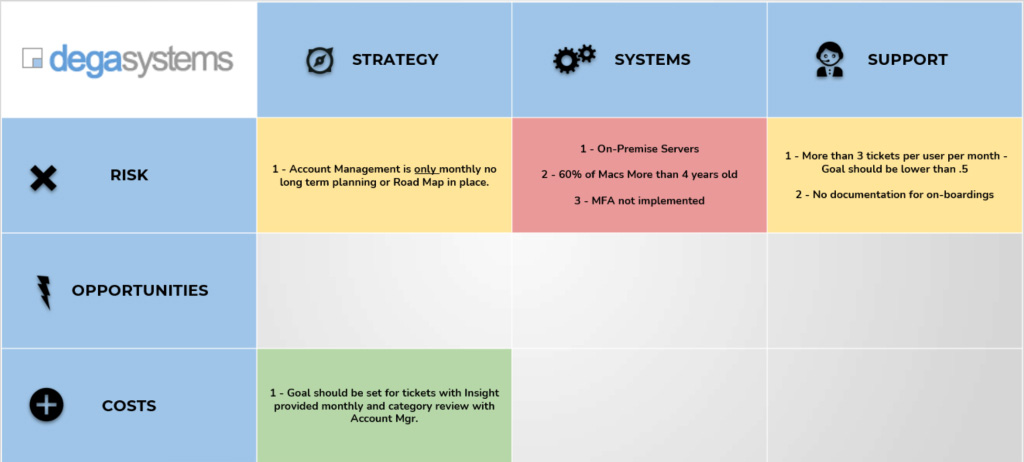
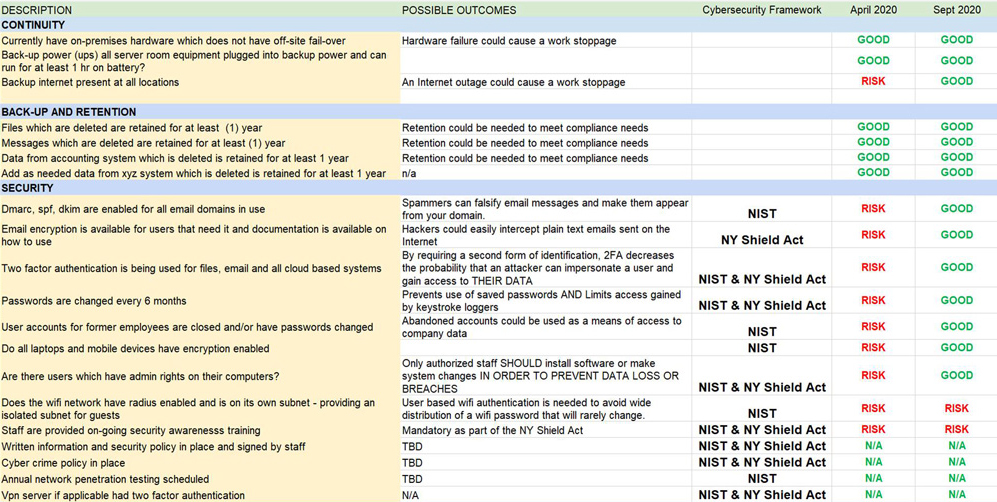
Our technology specific Strengths, Weaknesses, Opportunities and Threats (SWOT) analysis, which helps reveal your greatest IT vulnerabilities.
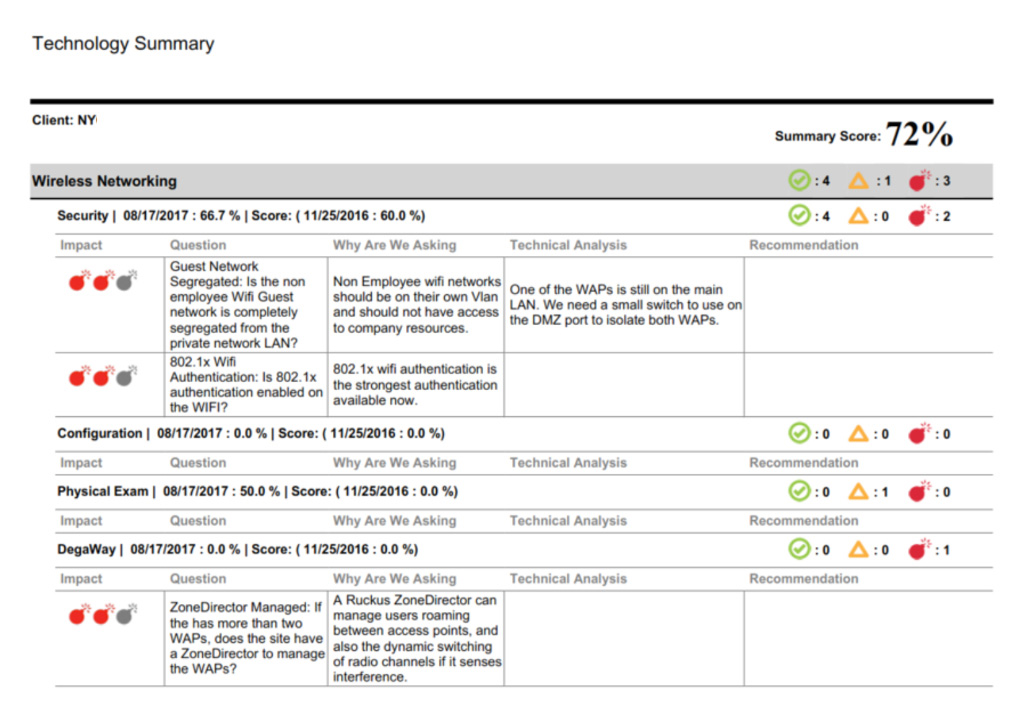
Our Technology Summary Scorecard that measures your existing IT systems and processes against established benchmarks and security frameworks. Then, we provide sound recommendations based on your unique needs.
3. Plan
What do you need in your roadmap to success?
This is where we take all your gathered IT information and use it to create your “technology roadmap.” It’s the plan that will take your IT services from sputtering to successful.
4. Execute
5. Optimize
How can we continue to increase your productivity and improve your security?
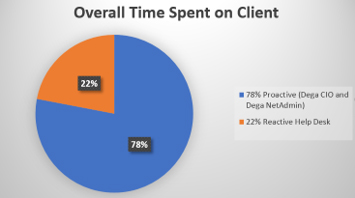
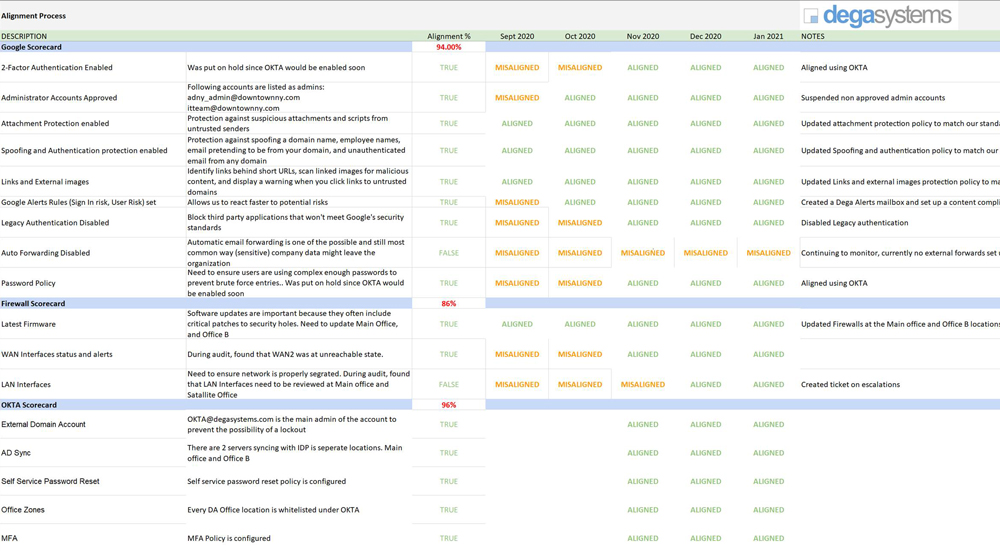
After we’ve put the alignment process in place and addressed your top IT priorities, we continue to work through your roadmap, strengthening your IT systems and security. Our purpose is to continuously monitor and maintain your IT systems to ensure it continues to function optimally while keeping your people, data and devices protected.
“The Tech Alignment Process and Manager (TAM) has been outstandingly useful for us. It provides a methodological and thorough look at our services and how they can be made more secure. It has dramatically improved our overall service. It’s also reduced our threat surface by implementing best practices, configurations and scheduling regular meeting updates to support findings and senior management.”
– Mark Poole, Great Bowery